CCTV News:Recently, there have been many cases of computer ransomware in China, especially in medical, educational and financial industries. Many individual users’ data files cannot be opened after being encrypted by ransomware.
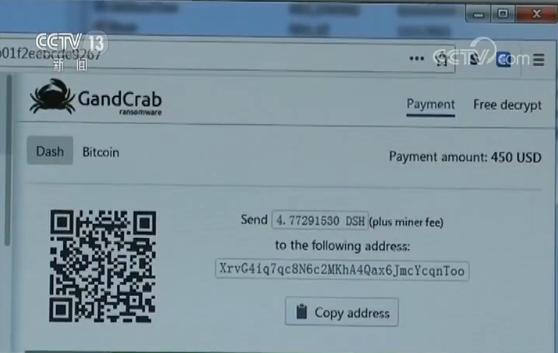
According to the intercepted ransomware samples, the virus mainly spreads through mobile storage devices and malware installation packages. After the user activates or opens the Trojan horse program containing ransomware, all files in the computer will be encrypted, and the user is required to pay the ransom within a limited time.
Wang Liang, a network security expert, said that after being infected with this ransomware, the first feeling of users was that their desktop background was suddenly changed. For example, their Word document photos could not be opened and the file extension was modified. Generally speaking, its blackmail amount is between 350 and 500 dollars.

In addition to infecting the software in the computer, this ransomware also targeted intelligent hardware including routers and smart cameras. According to the newly released Network Security Analysis Report of Typical Intelligent Hardware Devices, routers have become the most vulnerable intelligent hardware products to virus attacks, and privacy leakage, payment security and virus attacks have become the three major issues that users are most concerned about.
Chai Kunzhe, an expert in intelligent hardware, said that if a hacker hacked into your router, it would be equivalent to entering the virtual door of the network in your whole home. It can be associated with your equipment, all your smart devices and all your network devices, and it can also produce attacks.
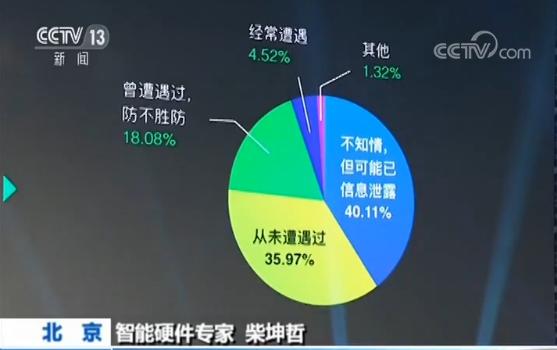
According to the characteristics of this ransomware, experts suggest that computer users must get into the habit of backing up important data and files, at the same time, they should raise their awareness of daily operation and maintenance safety and do a good job in data security prevention.
Wang Liang, a network security expert, said, don’t use weak password, that is, for example, don’t make your login password too simple, and then you should put security patches on your computer and update the software in time. Don’t add trust or release files blocked by security software, but download and install the software through formal channels.